Tools Covered in this Course
Course Details
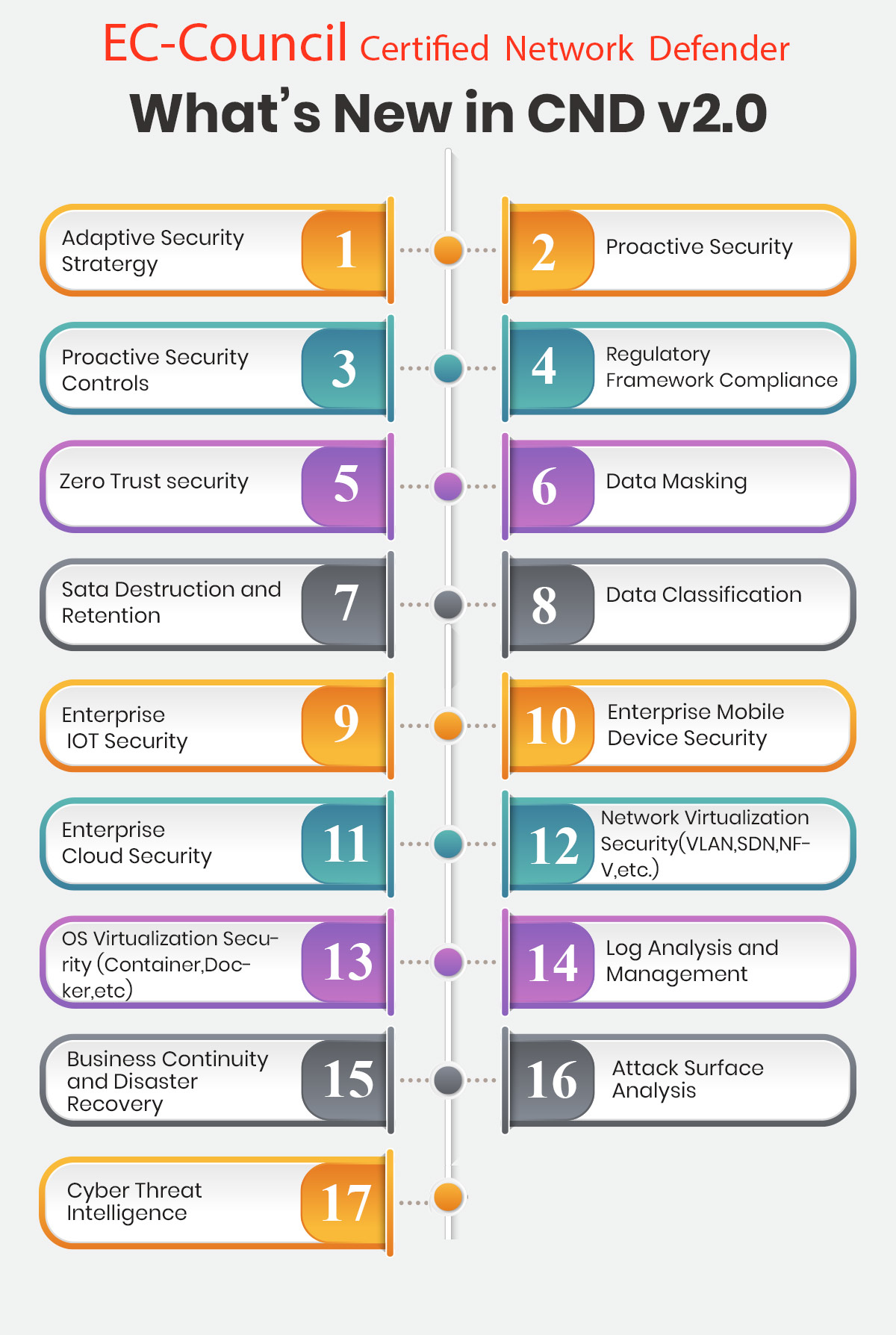
The Certified Network Defender v2 program has been upgraded and loaded with battle-ready ammunition to help Blue Teams defend and win the war against network breaches. Individuals and corporations looking to strengthen their Network Defense Skills will find CND v2 a must-have for 5 reasons:
- Only comprehensive network defense program built to incorporate critical secure network skills – Protect, Detect, Respond and Predict
- Maps to NICE 2.0 Framework
- Comes packed with the latest tools, technologies, and techniques
- Deploys a hands-on approach to learning
- Designed with an enhanced focus on Threat Prediction, Business Continuity, and Disaster Recovery
Who Is It For?
- Network Administrators
- Network Security Administrators
- Network Security Engineer
- Network Defense Technicians
- CND Analyst
- Security Analyst
- Security Operator
- Anyone who involves in network operations
What will you learn?
- Understanding network security management
- Establishing network security policies and procedures
- Windows and Linux security administration
- Setting up mobile and IoT device security
- Implementing data security techniques on networks
- Embedding virtualization technology security
- Determining cloud and wireless security
- Deploying and using risk assessment tools
- Learn basics of first response and forensics
- Understanding Indicators of Compromise, Attack, and Exposures (IoC, IoA, IoE)
- Building threat intelligence capabilities
- Establishing and monitoring log management
- Implementing endpoint security
- Configuring optimum firewall solutions
- Understanding and using IDS/IPS technologies
- Establishing Network Authentication, Authorization, Accounting (AAA)
Why Certified Network Defender?
Organizational focus on cyber defense is more important than ever as cyber breaches have a far greater financial impact and can cause broad reputational damage.
Despite the best efforts to prevent breaches, many organizations are still being compromised. Therefore organizations must have, as part of their defense mechanisms, trained network engineers who are focused on protecting, detecting, and responding to the threats on their networks.
Network administrators spend a lot of time with network environments and are familiar with network components, traffic, performance and utilization, network topology, location of each system, security policy, etc.
So, organizations can be much better in defending themselves from vicious attacks if the IT and network administrators equipped with adequate network security skills. Thus Network administrators can play a significant role in network defense and become the first line of defense for any organization.
What are the Domains of CND?
Course Outline
- Module 01: Network Attacks and Defense Strategies
- Module 02: Administrative Network Security
- Module 03: Technical Network Security
- Module 04: Network Perimeter Security
- Module 05: Endpoint Security-Windows Systems
- Module 06: Endpoint Security-Linux Systems
- Module 07: Endpoint Security- Mobile Devices
- Module 08: Endpoint Security-IoT Devices
- Module 09: Administrative Application Security
- Module 10: Data Security
- Module 11: Enterprise Virtual Network Security
- Module 12: Enterprise Cloud Network Security
- Module 13: Enterprise Wireless Network Security
- Module 14: Network Traffic Monitoring and Analysis
- Module 15: Network Logs Monitoring and Analysis
- Module 16: Incident Response and Forensic Investigation
- Module 17: Business Continuity and Disaster Recovery
- Module 18: Risk Anticipation with Risk Management
- Module 19: Threat Assessment with Attack Surface Analysis
- Module 20: Threat Prediction with Cyber Threat Intelligence
